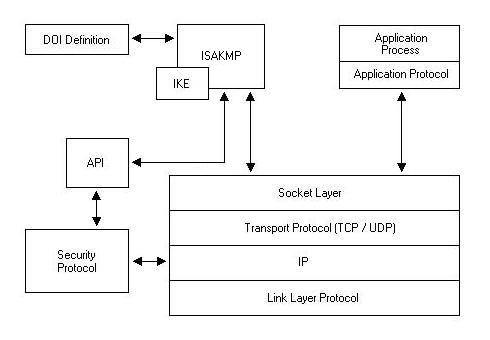
Components of IPSEC - CCIE IP SEC - Main Components of IP SEC - IKE, ESP and AH - Networkers Home - YouTube

Resolution of ISAKMP/Oakley key-agreement protocol resistant against denial-of-service attack | Semantic Scholar

IPSec Key Management|Oakley Key|ISAKMP Protocol|Lecture-02|Bca 6th Sem|By Sarvesh Sir|IICS College - YouTube

Oakley Wind Jacket - Tom Cruise - Mission: Impossible – Ghost Protocol | Sunglasses ID - celebrity sunglasses

Internet Key Exchange (IKE) and Security Association (SA) by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

Modified Protocols for Internet Key Exchange (IKE) Using Public Encryption and Signature Keys | Semantic Scholar

Oakley Wind Jacket - Tom Cruise - Mission: Impossible – Ghost Protocol | Sunglasses ID - celebrity sunglasses
Network Working Group H. Orman Request for Comments: 2412 Department of Computer Science Category: Informational Uni